Training course on Digital Identity Management and Beneficiary Verification
Training Course on Digital Identity Management and Beneficiary Verification is meticulously designed to equip aspiring and current social protection program managers with the advanced theoretical insights and intensive practical tools
Skills Covered
Course Overview
Training Course on Digital Identity Management and Beneficiary Verification
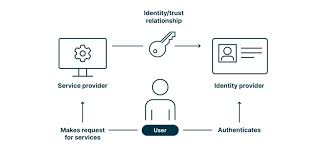
Introduction
Digital Identity Management and Beneficiary Verification is a crucial and rapidly evolving field, particularly vital for the efficient, secure, and inclusive delivery of social protection services and other digital public goods. In an increasingly digital world, establishing and verifying the unique identity of individuals is fundamental to preventing fraud, ensuring accurate targeting, and streamlining access to essential services. This discipline encompasses the design, implementation, and governance of digital identity systems, alongside the application of various technologies and methodologies for verifying who a beneficiary is. For governments, humanitarian organizations, financial institutions, and technology providers, mastering digital identity and verification is paramount for building trust, enhancing operational efficiency, and ensuring that vital support reaches those who truly need it, while upholding privacy and human rights.
Training Course on Digital Identity Management and Beneficiary Verification is meticulously designed to equip aspiring and current social protection program managers with the advanced theoretical insights and intensive practical tools necessary to excel in Digital Identity Management and Beneficiary Verification. We will delve into the foundational concepts of digital identity, master the intricacies of various verification technologies (biometric and non-biometric), and explore cutting-edge approaches to designing inclusive, secure, and privacy-preserving identity systems. A significant focus will be placed on understanding ethical considerations, mitigating risks, ensuring data protection, and navigating the practical challenges of implementing digital identity solutions in diverse contexts. By integrating industry best practices, analyzing real-world complex case studies, and engaging in hands-on design and policy formulation exercises, attendees will develop the strategic acumen to confidently lead and implement robust digital identity and verification frameworks, fostering unparalleled efficiency, security, and inclusion in digital service delivery.
Course Objectives
Upon completion of this course, participants will be able to:
- Analyze the fundamental concepts of digital identity, its components, and its critical role in modern digital services.
- Comprehend the purpose and strategic importance of beneficiary verification in social protection programs and beyond.
- Master the various biometric verification technologies (e.g., fingerprint, facial recognition, iris scan), their applications, and limitations.
- Develop expertise in utilizing non-biometric digital verification methods (e.g., credential-based, mobile-based, document verification).
- Formulate and implement robust strategies for data privacy, security, and ethical data governance of digital identity information.
- Identify and mitigate ethical considerations and potential biases in the design and deployment of digital identity systems.
- Understand the operational and institutional challenges associated with implementing large-scale digital identity and verification solutions.
- Design and apply human-centered design principles to create inclusive and accessible digital identity services for all populations.
- Evaluate interoperability requirements for digital identity systems with existing national databases and service platforms.
- Analyze the cost-benefit implications and return on investment of investing in digital identity and verification infrastructure.
- Explore the role of multi-stakeholder partnerships (public, private, civil society) in fostering successful digital identity ecosystems.
- Examine global best practices and lessons learned from successful digital identity and beneficiary verification initiatives.
- Prepare for and respond to fraud risks and security incidents related to digital identity and verification processes.
Target Audience
This course is essential for professionals involved in verifying and ensuring the quality of real estate appraisals:
- Social Protection Program Managers: Overseeing beneficiary registration and payment systems.
- Government Officials: Involved in national identity programs and digital public services.
- Digital Transformation Leads: Guiding the digitization of government and NGO services.
- Identity and Access Management (IAM) Specialists: Designing and managing identity systems.
- Cybersecurity Professionals: Focusing on the security of identity data and verification processes.
- Humanitarian Aid Workers: Implementing cash transfers and aid distribution in complex settings.
- Financial Inclusion Specialists: Linking identity to access to financial services.
- Technology Solution Providers: Developing digital identity and verification platforms.
Course Duration: 5 Days
Course Modules
Module 1: Foundations of Digital Identity
- Define digital identity, its core components, and its significance in the digital age.
- Distinguish between foundational (legal), functional (transactional), and portable identities.
- Explore the lifecycle of digital identity: enrollment, authentication, verification, and revocation.
- Discuss the benefits of robust digital identity: efficiency, security, and inclusion in service delivery.
- Introduce various digital identity models: centralized, federated, and self-sovereign identity.
Module 2: Beneficiary Verification in Social Protection
- Understand the primary purpose of beneficiary verification in social protection programs.
- Analyze the challenges and limitations of traditional, manual verification methods (e.g., paper-based).
- Examine the goals of digital verification: reducing fraud, minimizing inclusion/exclusion errors, and streamlining access.
- Identify different types of verification: initial enrollment, ongoing eligibility checks, and proof of presence.
- Discuss the legal and policy frameworks governing beneficiary data and verification processes.
Module 3: Biometric Verification Technologies
- Provide an overview of common biometric modalities: fingerprint, facial recognition, iris scanning, and voice biometrics.
- Explain the process of biometric data capture, template generation, storage, and matching.
- Highlight the advantages of biometrics: high accuracy, uniqueness, and convenience in large-scale programs.
- Address key challenges: accuracy rates, privacy concerns, consent issues, and accessibility for diverse populations.
- Review case studies of large-scale biometric identity systems (e.g., Aadhaar in India, national ID programs).
Module 4: Non-Biometric Digital Verification Methods
- Explore credential-based verification: utilizing national ID numbers, digital certificates, and unique identifiers.
- Examine knowledge-based authentication (KBA) and the use of challenge questions for identity confirmation.
- Discuss mobile-based verification strategies: leveraging SIM card registration, mobile money accounts, and SMS-based codes.
- Analyze document verification technologies: digital scanning, optical character recognition (OCR), and AI-powered authenticity checks.
- Understand the implementation and benefits of multi-factor authentication (MFA) for enhanced security.
Module 5: Data Privacy, Security, and Trust
- Emphasize the critical importance of data encryption for sensitive digital identity information.
- Implement secure data storage solutions and transmission protocols to protect beneficiary data.
- Ensure compliance with major data protection regulations (e.g., GDPR, national data protection laws).
- Develop robust mechanisms for obtaining informed consent for data collection, usage, and sharing.
- Formulate strategies for building and maintaining trust with beneficiaries regarding digital data handling and privacy.
Module 6: Ethical Considerations and Inclusive Design
- Identify and address potential biases inherent in digital identity systems and algorithms.
- Prioritize inclusive design to ensure accessibility for all populations, including persons with disabilities, the elderly, and those with low digital literacy.
- Discuss strategies for mitigating the risk of exclusion and preventing the creation of "digital orphans."
- Explore the fundamental human rights aspects of identity: the right to identity and the right to be forgotten.
- Apply human-centered design principles throughout the lifecycle of digital identity solutions.
Module 7: Implementation and Operational Challenges
- Assess the necessary infrastructure requirements for deploying and maintaining digital identity systems.
- Address challenges related to interoperability with existing government systems, databases, and service delivery platforms.
- Develop comprehensive strategies for capacity building and training for both program staff and beneficiaries.
- Conduct thorough cost-benefit analyses to justify investments in digital identity solutions.
- Establish effective mechanisms for managing grievance redressal and appeals processes for identity-related issues.
Module 8: Case Studies and Future Trends
- Analyze successful digital identity and beneficiary verification programs from diverse global contexts.
- Discuss lessons learned from both successful implementations and challenges encountered.
- Explore emerging trends in digital identity: Self-Sovereign Identity (SSI) and the role of blockchain technology.
- Investigate the increasing role of Artificial Intelligence (AI) in identity verification, fraud detection, and liveness checks.
- Consider the future of digital identity in a rapidly globalizing and interconnected world, including cross-border identity.
Training Methodology
- Interactive Workshops: Facilitated discussions, group exercises, and problem-solving activities.
- Case Studies: Real-world examples to illustrate successful community-based surveillance practices.
- Role-Playing and Simulations: Practice engaging communities in surveillance activities.
- Expert Presentations: Insights from experienced public health professionals and community leaders.
- Group Projects: Collaborative development of community surveillance plans.
- Action Planning: Development of personalized action plans for implementing community-based surveillance.
- Digital Tools and Resources: Utilization of online platforms for collaboration and learning.
- Peer-to-Peer Learning: Sharing experiences and insights on community engagement.
- Post-Training Support: Access to online forums, mentorship, and continued learning resources.
Register as a group from 3 participants for a Discount
Send us an email: info@datastatresearch.org or call +254724527104
Certification
Upon successful completion of this training, participants will be issued with a globally recognized certificate.
Tailor-Made Course
We also offer tailor-made courses based on your needs.
Key Notes
- Participants must be conversant in English.
- Upon completion of training, participants will receive an Authorized Training Certificate.
- The course duration is flexible and can be modified to fit any number of days.
- Course fee includes facilitation, training materials, 2 coffee breaks, buffet lunch, and a Certificate upon successful completion.
- One-year post-training support, consultation, and coaching provided after the course.
- Payment should be made at least a week before the training commencement to DATASTAT CONSULTANCY LTD account, as indicated in the invoice, to enable better preparation.