Training course on Risk Management and Mitigation in Social Protection Policies
Training Course on Risk Management and Mitigation in Social Protection Policies delves into nuanced methodologies for conducting comprehensive risk assessments across the social protection delivery chain
Course Overview
Training Course on Risk Management and Mitigation in Social Protection Policies
Introduction:
While social protection policies are designed to mitigate risks for vulnerable populations, their implementation inherently involves a range of operational, financial, ethical, and political risks that can undermine their effectiveness, efficiency, and legitimacy. From targeting errors and fraud to data breaches, political interference, and unintended market distortions, these risks must be systematically identified, assessed, and proactively managed. This course is meticulously designed to equip policymakers, social protection program managers, risk managers, internal auditors, M&E specialists, data governance professionals, and development practitioners with the expert knowledge and practical methodologies to identify, assess, mitigate, and monitor risks across the entire social protection policy lifecycle. The program focuses on the conceptual framework of risk management in social protection, risk identification and assessment, developing mitigation strategies, establishing robust control environments, managing fraud and corruption, ensuring data security and privacy, and building a culture of risk awareness, blending rigorous analytical frameworks with practical, hands-on application, global case studies (with a strong emphasis on African contexts, including Kenya), and interactive risk assessment and mitigation planning exercises. Participants will gain the strategic foresight and technical expertise to confidently lead the development and implementation of robust risk management frameworks, fostering unparalleled program integrity, efficiency, and public trust, thereby securing their position as indispensable leaders in building resilient and accountable social protection systems.
Training Course on Risk Management and Mitigation in Social Protection Policies delves into nuanced methodologies for conducting comprehensive risk assessments across the social protection delivery chain, mastering sophisticated techniques for designing internal control systems to prevent and detect fraud and errors, and exploring cutting-edge approaches to leveraging data analytics for proactive risk monitoring, developing incident response plans for cybersecurity breaches, establishing robust grievance redress mechanisms to address risks, and fostering an ethical environment to minimize political interference and elite capture. A significant focus will be placed on understanding the interplay of risk management with digital transformation in social protection, the specific challenges of managing risks in fragile and emergency contexts (as observed in Kenya's humanitarian operations), and the practical application of adaptive risk management to ensure policies can quickly adjust to emerging threats.
Course Objectives:
Upon completion of this course, participants will be able to:
- Analyze core concepts and strategic responsibilities of risk management and mitigation in social protection policies.
- Master sophisticated techniques for identifying, categorizing, and assessing various types of risks across the social protection program lifecycle.
- Develop robust methodologies for designing and implementing effective risk mitigation strategies for identified threats.
- Implement effective strategies for establishing and strengthening internal control environments to minimize operational and financial risks.
- Manage complex considerations for preventing, detecting, and responding to fraud and corruption in social protection programs.
- Apply robust strategies for ensuring data security, privacy, and integrity within social protection information systems.
- Understand the deep integration of grievance redress mechanisms and accountability frameworks in mitigating risks and building trust.
- Leverage knowledge of global best practices and lessons learned in risk management from social protection programs in diverse country contexts, including Kenya.
- Optimize strategies for promoting a culture of risk awareness and ethics among social protection staff and stakeholders.
- Formulate specialized recommendations for managing political, reputational, and systemic risks that can impact policy sustainability.
- Conduct comprehensive assessments of existing social protection policies and operations to identify inherent risks and control gaps.
- Navigate challenging situations such as resource constraints, data limitations, political interference, and external shocks in managing risks.
- Develop a holistic, proactive, and ethically grounded approach to risk management and mitigation in social protection policies, ensuring program integrity, effectiveness, and beneficiary protection.
Target Audience:
This course is designed for professionals interested in Risk Management and Mitigation in Social Protection Policies:
- Social Protection Program Managers: Overseeing operations and responsible for program integrity.
- Risk Managers & Internal Auditors: From government ministries, public agencies, and financial institutions.
- Policymakers & Senior Government Officials: Involved in social sector governance and accountability.1
- Data Governance & Cybersecurity Specialists: Protecting sensitive beneficiary data.
- Public Financial Management (PFM) Professionals: Ensuring efficient and secure use of public funds in social programs.
- Development Partners & UN Agency Staff: Supporting governments in strengthening social protection systems.
- M&E Specialists: Using data to identify risks and monitor mitigation effectiveness.
- Civil Society Organizations: Advocating for transparency and accountability in social protection.
Course Duration: 5 Days
Course Modules:
- Module 1: Foundations of Risk Management in Social Protection
- Defining Risk Management: Concepts, principles, and its importance in social protection.
- Types of Risks in Social Protection: Operational, financial, political, reputational, legal, ethical, data/cybersecurity.
- Risk Management Frameworks: Introduction to common methodologies (e.g., ISO 31000 principles, COSO ERM).
- The Risk Management Cycle: Identification, assessment, mitigation, monitoring, and review.2
- Benefits of Proactive Risk Management: Enhanced efficiency, accountability, public trust, and resilience.
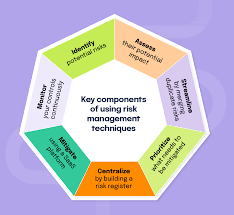
- Module 2: Risk Identification and Assessment Methodologies
- Techniques for Risk Identification: Brainstorming, checklists, interviews, process mapping, historical data analysis.3
- Developing a Risk Register: Documenting identified risks, their descriptions, and potential impacts.4
- Risk Assessment: Analyzing likelihood and impact (severity) of identified risks.
- Risk Prioritization Matrix: Categorizing risks by high, medium, and low levels for focused attention.5
- Contextual Risk Analysis: Adapting risk assessment to specific country contexts (e.g., Kenya's unique challenges).
- Module 3: Developing and Implementing Risk Mitigation Strategies
- Risk Treatment Options: Avoid, reduce, transfer, or accept risks.
- Designing Mitigation Measures: Specific actions to reduce likelihood or impact.6
- Internal Controls: Segregation of duties, authorizations, reconciliations, physical controls.7
- Policy Design Elements for Mitigation: Self-targeting mechanisms, payment frequency, program rules.
- Contingency Planning: Preparing for high-impact, low-likelihood risks.
- Module 4: Managing Fraud and Corruption Risks
- Understanding Types of Fraud and Corruption: Beneficiary fraud, staff fraud, vendor fraud, collusion.
- Fraud Risk Assessment: Identifying vulnerabilities and red flags.8
- Prevention Strategies: Strong internal controls, transparency, public awareness campaigns.
- Detection Methods: Data analytics, whistleblower hotlines, regular audits, field verification.
- Response and Investigation: Developing clear protocols for reporting, investigation, and recovery.
- Module 5: Data Security, Privacy, and Cyber Risk Mitigation
- Importance of Data Protection: Protecting sensitive beneficiary information (e.g., in Kenya's SPIS).
- Data Privacy Principles: Collection limitation, data minimization, accuracy, storage limitation.9
- Cybersecurity Threats: Hacking, malware, phishing, data breaches.
- Mitigation Strategies: Encryption, access controls, regular security audits, staff training.
- Incident Response Planning: Protocols for identifying, containing, and recovering from cyber incidents.
- Module 6: Institutionalizing Risk Management and Governance
- Roles and Responsibilities: Establishing clear roles for risk ownership and oversight within government.
- Developing a Risk Management Policy and Manual: Guiding principles and procedures.
- Risk Reporting and Communication: Regular updates to management and stakeholders.10
- Building a Culture of Risk Awareness: Training, incentives, and leadership commitment.
- Integrating Risk Management into Operations: Embedding it in daily processes and decision-making.
- Module 7: Political, Reputational, and Systemic Risk Management
- Political Risks: Changes in government, policy shifts, elite capture, budget cuts.
- Reputational Risks: Negative public perception, media scrutiny, loss of public trust.11
- Systemic Risks: Fragmented systems, lack of interoperability, weak institutional capacity.
- Mitigation Strategies: Strategic communication, stakeholder engagement, policy advocacy, system strengthening.
- Crisis Management and Communication: Responding effectively to unforeseen events.
- Module 8: Practical Application: Developing a Risk Mitigation Plan
- Case Study Analysis: Participants analyze a real-world social protection program and its inherent risks (e.g., a specific cash transfer program in Kenya).
- Risk Workshop: Participants work in groups to identify and assess key risks for the chosen case study.
- Developing a Risk Mitigation Plan: Proposing specific, actionable strategies for each identified risk.
- Monitoring and Reporting Framework: Designing how the mitigation efforts would be tracked and communicated.
- Presentation and Peer Review: Participants present their risk mitigation plans and receive feedback.
Training Methodology
- Interactive Workshops: Facilitated discussions, group exercises, and problem-solving activities.
- Case Studies: Real-world examples to illustrate successful community-based surveillance practices.
- Role-Playing and Simulations: Practice engaging communities in surveillance activities.
- Expert Presentations: Insights from experienced public health professionals and community leaders.
- Group Projects: Collaborative development of community surveillance plans.
- Action Planning: Development of personalized action plans for implementing community-based surveillance.
- Digital Tools and Resources: Utilization of online platforms for collaboration and learning.
- Peer-to-Peer Learning: Sharing experiences and insights on community engagement.
- Post-Training Support: Access to online forums, mentorship, and continued learning resources.
Register as a group from 3 participants for a Discount
Send us an email: info@datastatresearch.org or call +254724527104
Certification
Upon successful completion of this training, participants will be issued with a globally recognized certificate.
Tailor-Made Course
We also offer tailor-made courses based on your needs.
Key Notes
- Participants must be conversant in English.