Digital Forensics Courses
Comprehensive Digital Forensics training programs for professionals
Comprehensive Digital Forensics training programs for professionals

Training Course on Building a Threat Hunting Team and Program focuses on empowering security professionals with the knowledge, skills, and methodologies to establish, operate, and mature a dedicated threat hunting team and program.
Training Course on Building a Threat Hunting Team and Program focuses on empowering security professionals with the knowledge, skills, and methodologies to establish, operate, and mature a dedicated threat hunting team and program.

Training Course on Advanced Log Correlation for Threat Detection provides cybersecurity professionals with the advanced skills to leverage log data effectively for proactive threat detection and rapid incident response.
Training Course on Advanced Log Correlation for Threat Detection provides cybersecurity professionals with the advanced skills to leverage log data effectively for proactive threat detection and rapid incident response.

Training Course on Hunting for Adversary Lateral Movement provides blue teams, security analysts, and incident responders with the proactive defense strategies and detection engineering skills necessary to identify, analyze, and neutralize lateral movement, effectively diminishing dwell time and mitigating breach impact.
Training Course on Hunting for Adversary Lateral Movement provides blue teams, security analysts, and incident responders with the proactive defense strategies and detection engineering skills necessary to identify, analyze, and neutralize lateral movement, effectively diminishing dwell time and mitigating breach impact.

Training Course on Endpoint Detection and Response for Threat Hunting empowers cybersecurity professionals to proactively hunt threats, investigate incidents, and fortify organizational resilience
Training Course on Endpoint Detection and Response for Threat Hunting empowers cybersecurity professionals to proactively hunt threats, investigate incidents, and fortify organizational resilience
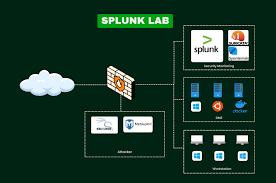
Training Course on Custom Threat Hunting Queries (Splunk, ELK) empowers cybersecurity professionals with the essential skills to develop and implement custom threat hunting queries using industry-leading Security Information and Event Management (SIEM) platforms, specifically Splunk and the ELK Stack (Elasticsearch, Logstash, Kibana).
Training Course on Custom Threat Hunting Queries (Splunk, ELK) empowers cybersecurity professionals with the essential skills to develop and implement custom threat hunting queries using industry-leading Security Information and Event Management (SIEM) platforms, specifically Splunk and the ELK Stack (Elasticsearch, Logstash, Kibana).

Training Course on Deception Technologies and Honeypots for Threat Hunting provides cybersecurity professionals with the cutting-edge skills and knowledge to proactively detect, analyze, and neutralize these elusive threats.
Training Course on Deception Technologies and Honeypots for Threat Hunting provides cybersecurity professionals with the cutting-edge skills and knowledge to proactively detect, analyze, and neutralize these elusive threats.
Training Course on Attacker Tactics, Techniques, and Procedures Analysis is meticulously designed to equip cybersecurity professionals with the advanced knowledge and practical skills required to dissect, analyze, and anticipate the actions of sophisticated threat actors.
Training Course on Attacker Tactics, Techniques, and Procedures Analysis is meticulously designed to equip cybersecurity professionals with the advanced knowledge and practical skills required to dissect, analyze, and anticipate the actions of sophisticated threat actors.

Training Course on Behavioral Analytics for Insider Threat Hunting is designed to empower cybersecurity professionals with the advanced techniques of User and Entity Behavior Analytics (UEBA).
Training Course on Behavioral Analytics for Insider Threat Hunting is designed to empower cybersecurity professionals with the advanced techniques of User and Entity Behavior Analytics (UEBA).
Training Course on Cloud Log Analysis and Correlation for Investigations offers a comprehensive, hands-on approach to understanding how log data from cloud platforms can be analyzed and correlated for effective forensic investigations.
Training Course on Cloud Log Analysis and Correlation for Investigations offers a comprehensive, hands-on approach to understanding how log data from cloud platforms can be analyzed and correlated for effective forensic investigations.

Training Course on Network Device Forensics equips cybersecurity professionals, network engineers, and IT investigators with the skills to analyze, interpret, and investigate digital artifacts within critical infrastructure components.
Training Course on Network Device Forensics equips cybersecurity professionals, network engineers, and IT investigators with the skills to analyze, interpret, and investigate digital artifacts within critical infrastructure components.
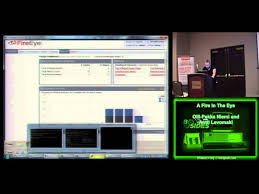
Training Course on Advanced Network Traffic Analysis focuses on PCAP (Packet Capture) analysis, a foundational technique for understanding and interpreting network behavior.
Training Course on Advanced Network Traffic Analysis focuses on PCAP (Packet Capture) analysis, a foundational technique for understanding and interpreting network behavior.

Training Course on Network Intrusion Detection and Analysis equips cybersecurity professionals, system administrators, and IT managers with the skills to detect, analyze, and respond to network-based attacks in real-time.
Training Course on Network Intrusion Detection and Analysis equips cybersecurity professionals, system administrators, and IT managers with the skills to detect, analyze, and respond to network-based attacks in real-time.