Digital Forensics Courses
Comprehensive Digital Forensics training programs for professionals
Comprehensive Digital Forensics training programs for professionals

Training Course on Malware Triage and Classification Automation empowers cybersecurity professionals with the skills and tools to automate and accelerate malware identification, classification, and response processes using cutting-edge technologies like machine learning, sandboxing, YARA rules, and behavioral analytics.
Training Course on Malware Triage and Classification Automation empowers cybersecurity professionals with the skills and tools to automate and accelerate malware identification, classification, and response processes using cutting-edge technologies like machine learning, sandboxing, YARA rules, and behavioral analytics.

Training Course on Analyzing Advanced Persistent Threat (APT) Malware is designed to equip cybersecurity professionals with advanced skills to detect, analyze, and mitigate APT malware using cutting-edge threat intelligence tools and reverse engineering techniques.
Training Course on Analyzing Advanced Persistent Threat (APT) Malware is designed to equip cybersecurity professionals with advanced skills to detect, analyze, and mitigate APT malware using cutting-edge threat intelligence tools and reverse engineering techniques.

Training Course on Understanding Exploit Kits and Exploit Analysis is designed to equip participants with the expertise to detect, analyze, and mitigate risks associated with exploit kits across multiple environments.
Training Course on Understanding Exploit Kits and Exploit Analysis is designed to equip participants with the expertise to detect, analyze, and mitigate risks associated with exploit kits across multiple environments.

Training Course on Anti-Reverse Engineering Techniques and Countermeasures is meticulously designed to equip cybersecurity professionals, developers, and digital defenders with cutting-edge knowledge and hands-on skills.
Training Course on Anti-Reverse Engineering Techniques and Countermeasures is meticulously designed to equip cybersecurity professionals, developers, and digital defenders with cutting-edge knowledge and hands-on skills.

Training Course on Data Privacy Regulations and Their Impact on Digital Forensics and Incident Response provides practical, hands-on training on integrating privacy-by-design principles into forensic methodologies and breach response frameworks
Training Course on Data Privacy Regulations and Their Impact on Digital Forensics and Incident Response provides practical, hands-on training on integrating privacy-by-design principles into forensic methodologies and breach response frameworks

Training Course on Digital Forensics for Legal Professionals and Prosecutors is meticulously designed to bridge the gap between legal theory and forensic practice. Participants will delve into the technical aspects of digital investigations while grounding their learning in legal frameworks and ethical considerations.
Training Course on Digital Forensics for Legal Professionals and Prosecutors is meticulously designed to bridge the gap between legal theory and forensic practice. Participants will delve into the technical aspects of digital investigations while grounding their learning in legal frameworks and ethical considerations.

Training Course on Ethics in Digital Forensics and Investigation delves into the fundamental ethical principles that govern digital evidence collection, preservation, analysis, and presentation.
Training Course on Ethics in Digital Forensics and Investigation delves into the fundamental ethical principles that govern digital evidence collection, preservation, analysis, and presentation.
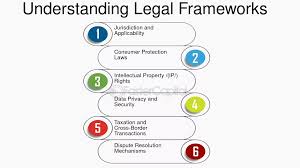
Training Course on Cross-Border Investigations and International Legal Frameworks is meticulously designed to equip participants with the advanced skills and strategic insights required to manage complex international cases, from initial detection to successful resolution.
Training Course on Cross-Border Investigations and International Legal Frameworks is meticulously designed to equip participants with the advanced skills and strategic insights required to manage complex international cases, from initial detection to successful resolution.

Training Course on Developing a Cyber Incident Disclosure Strategy is meticulously designed to empower organizations to navigate the complexities of incident disclosure, ensuring compliance with evolving regulations, fostering stakeholder confidence, and maintaining a security-first posture in a volatile digital world.
Training Course on Developing a Cyber Incident Disclosure Strategy is meticulously designed to empower organizations to navigate the complexities of incident disclosure, ensuring compliance with evolving regulations, fostering stakeholder confidence, and maintaining a security-first posture in a volatile digital world.

Training Course on Ethical Hacking and Penetration Testing for Digital Forensics and Incident Response Readiness is meticulously designed to equip cybersecurity professionals with the advanced offensive and defensive skills necessary to proactively identify, exploit, and mitigate vulnerabilities, thereby significantly enhancing an organization's Incident Response Readiness.
Training Course on Ethical Hacking and Penetration Testing for Digital Forensics and Incident Response Readiness is meticulously designed to equip cybersecurity professionals with the advanced offensive and defensive skills necessary to proactively identify, exploit, and mitigate vulnerabilities, thereby significantly enhancing an organization's Incident Response Readiness.
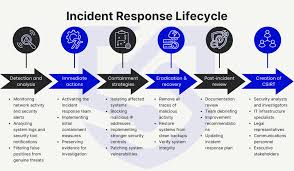
Training Course on Incident Response Reporting for Compliance and Stakeholders is designed to equip professionals with the essential skills and knowledge to navigate the complexities of incident response reporting, ensuring compliance with legal and regulatory requirements while maintaining stakeholder trust.
Training Course on Incident Response Reporting for Compliance and Stakeholders is designed to equip professionals with the essential skills and knowledge to navigate the complexities of incident response reporting, ensuring compliance with legal and regulatory requirements while maintaining stakeholder trust.

Training Course on the Admissibility of Digital Evidence in Court is meticulously designed to equip participants with the critical knowledge and practical skills to ensure that digital evidence is not just collected, but is also legally sound, authenticated, and persuasively presented in a court of law.
Training Course on the Admissibility of Digital Evidence in Court is meticulously designed to equip participants with the critical knowledge and practical skills to ensure that digital evidence is not just collected, but is also legally sound, authenticated, and persuasively presented in a court of law.