Digital Forensics Courses
Comprehensive Digital Forensics training programs for professionals
Comprehensive Digital Forensics training programs for professionals

Training Course on Open-Source Intelligence for Threat Hunting provides cybersecurity professionals with the essential skills and cutting-edge methodologies to leverage Open-Source Intelligence (OSINT) for proactive threat hunting.
Training Course on Open-Source Intelligence for Threat Hunting provides cybersecurity professionals with the essential skills and cutting-edge methodologies to leverage Open-Source Intelligence (OSINT) for proactive threat hunting.
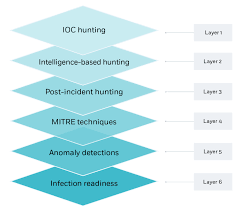
Training Course on Proactive Threat Hunting Methodologies equips cybersecurity professionals with the cutting-edge skills and strategic mindset required to proactively detect, analyze, and neutralize hidden threats before they escalate into major incidents.
Training Course on Proactive Threat Hunting Methodologies equips cybersecurity professionals with the cutting-edge skills and strategic mindset required to proactively detect, analyze, and neutralize hidden threats before they escalate into major incidents.

Training Course on Machine Learning for Anomaly Detection in Threat Hunting focuses on practical applications, bridging the gap between theoretical ML concepts and real-world security operations center (SOC) challenges, ultimately enhancing an organization's cyber
Training Course on Machine Learning for Anomaly Detection in Threat Hunting focuses on practical applications, bridging the gap between theoretical ML concepts and real-world security operations center (SOC) challenges, ultimately enhancing an organization's cyber
Training Course on Security Data Science for Threat Hunting is designed to bridge the gap between cybersecurity operations and advanced analytics. Participants will gain hands-on experience with big data platforms, learn to leverage AI for security analytics, and master the art of transforming raw security logs into actionable threat intelligence
Training Course on Security Data Science for Threat Hunting is designed to bridge the gap between cybersecurity operations and advanced analytics. Participants will gain hands-on experience with big data platforms, learn to leverage AI for security analytics, and master the art of transforming raw security logs into actionable threat intelligence

Training Course on Threat Hunting with Sysmon and Windows Event Logs empowers cybersecurity professionals with the essential skills and methodologies to proactively hunt for malicious activity, minimize dwell time, and significantly bolster their organizational security posture.
Training Course on Threat Hunting with Sysmon and Windows Event Logs empowers cybersecurity professionals with the essential skills and methodologies to proactively hunt for malicious activity, minimize dwell time, and significantly bolster their organizational security posture.
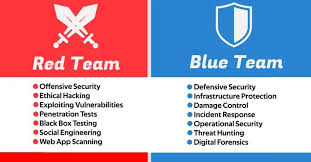
Training Course on Red Team and Blue Team Operations for Threat Hunters provides cybersecurity professionals with the cutting-edge knowledge and hands-on skills required to excel in modern threat hunting.
Training Course on Red Team and Blue Team Operations for Threat Hunters provides cybersecurity professionals with the cutting-edge knowledge and hands-on skills required to excel in modern threat hunting.

Training Course on Hunting for Persistence Mechanisms is meticulously designed for cyber defense professionals seeking to master threat hunting for these elusive mechanisms across various operating systems, thereby significantly enhancing an organization's resilience against advanced attacks and reducing dwell time
Training Course on Hunting for Persistence Mechanisms is meticulously designed for cyber defense professionals seeking to master threat hunting for these elusive mechanisms across various operating systems, thereby significantly enhancing an organization's resilience against advanced attacks and reducing dwell time

Training Course on MITRE ATT and CK Framework for Threat Hunting provides cybersecurity professionals with the essential knowledge and practical skills to leverage the MITRE ATT&CK Framework for advanced threat hunting.
Training Course on MITRE ATT and CK Framework for Threat Hunting provides cybersecurity professionals with the essential knowledge and practical skills to leverage the MITRE ATT&CK Framework for advanced threat hunting.

Training Course on Hunting for Fileless Malware and Living Off the Land Attacks focuses on behavioral analytics, memory forensics, and endpoint detection and response (EDR) strategies to uncover hidden malicious activity
Training Course on Hunting for Fileless Malware and Living Off the Land Attacks focuses on behavioral analytics, memory forensics, and endpoint detection and response (EDR) strategies to uncover hidden malicious activity
Training Course on Network Threat Hunting Techniques and Tools provides security professionals with the essential methodologies, cutting-edge tools, and strategic mindset required to move beyond reactive defense, enabling them to identify subtle indicators of compromise (IOCs) and adversary tactics, techniques, and procedures (TTPs) before significant damage occurs.
Training Course on Network Threat Hunting Techniques and Tools provides security professionals with the essential methodologies, cutting-edge tools, and strategic mindset required to move beyond reactive defense, enabling them to identify subtle indicators of compromise (IOCs) and adversary tactics, techniques, and procedures (TTPs) before significant damage occurs.

Training Course on Cloud Environment Threat Hunting provides a comprehensive deep dive into proactive cybersecurity strategies for Cloud Environments, equipping security professionals with the essential skills and methodologies for threat detection and incident response.
Training Course on Cloud Environment Threat Hunting provides a comprehensive deep dive into proactive cybersecurity strategies for Cloud Environments, equipping security professionals with the essential skills and methodologies for threat detection and incident response.
Training Course on Cyber Threat Intelligence for Proactive Defense delves into the foundational principles and advanced practices of CTI, equipping participants with the knowledge and skills to build robust threat intelligence programs. From data collection and analysis to threat hunting and strategic intelligence dissemination, the course covers the entire CTI lifecycle.
Training Course on Cyber Threat Intelligence for Proactive Defense delves into the foundational principles and advanced practices of CTI, equipping participants with the knowledge and skills to build robust threat intelligence programs. From data collection and analysis to threat hunting and strategic intelligence dissemination, the course covers the entire CTI lifecycle.