Edr Courses
Explore instructor-led and hybrid programs aligned to practical Edr use cases across industries.
Available Edr Courses
Showing 1-7 of 7 courses

Digital Forensics
Training Course on Advanced Wireless Attack Forensics is specifically designed to equip cybersecurity professionals, digital forensic analysts, and network investigators with the latest tools, skills, and methodologies required to detect, analyze, and respond to sophisticated wireless-based cyberattacks.
10 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Training Course on Advanced Wireless Attack Forensics is specifically designed to equip cybersecurity professionals, digital forensic analysts, and network investigators with the latest tools, skills, and methodologies required to detect, analyze, and respond to sophisticated wireless-based cyberattacks.
10 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Digital Forensics
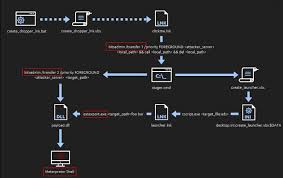
Training Course on Detecting Fileless Malware and Living-Off-The-Land Binaries is designed for cybersecurity professionals, SOC analysts, incident responders, and threat hunters who are looking to enhance their advanced threat detection skill set.
10 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Training Course on Detecting Fileless Malware and Living-Off-The-Land Binaries is designed for cybersecurity professionals, SOC analysts, incident responders, and threat hunters who are looking to enhance their advanced threat detection skill set.
10 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore

Digital Forensics
Training Course on Hunting for Fileless Malware and Living Off the Land Attacks focuses on behavioral analytics, memory forensics, and endpoint detection and response (EDR) strategies to uncover hidden malicious activity
5 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Training Course on Hunting for Fileless Malware and Living Off the Land Attacks focuses on behavioral analytics, memory forensics, and endpoint detection and response (EDR) strategies to uncover hidden malicious activity
5 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore

Digital Forensics
Training Course on Hunting for Persistence Mechanisms is meticulously designed for cyber defense professionals seeking to master threat hunting for these elusive mechanisms across various operating systems, thereby significantly enhancing an organization's resilience against advanced attacks and reducing dwell time
5 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Training Course on Hunting for Persistence Mechanisms is meticulously designed for cyber defense professionals seeking to master threat hunting for these elusive mechanisms across various operating systems, thereby significantly enhancing an organization's resilience against advanced attacks and reducing dwell time
5 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Digital Forensics
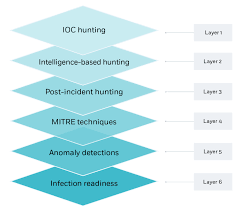
Training Course on Network Threat Hunting Techniques and Tools provides security professionals with the essential methodologies, cutting-edge tools, and strategic mindset required to move beyond reactive defense, enabling them to identify subtle indicators of compromise (IOCs) and adversary tactics, techniques, and procedures (TTPs) before significant damage occurs.
10 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Training Course on Network Threat Hunting Techniques and Tools provides security professionals with the essential methodologies, cutting-edge tools, and strategic mindset required to move beyond reactive defense, enabling them to identify subtle indicators of compromise (IOCs) and adversary tactics, techniques, and procedures (TTPs) before significant damage occurs.
10 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Digital Forensics
Training Course on Proactive Threat Hunting Methodologies equips cybersecurity professionals with the cutting-edge skills and strategic mindset required to proactively detect, analyze, and neutralize hidden threats before they escalate into major incidents.
10 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Training Course on Proactive Threat Hunting Methodologies equips cybersecurity professionals with the cutting-edge skills and strategic mindset required to proactively detect, analyze, and neutralize hidden threats before they escalate into major incidents.
10 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore

Digital Forensics
Training Course on Threat Hunting with Malware Analysis Techniques is designed to equip cybersecurity professionals with hands-on skills in proactive threat detection and malware reverse engineering.
5 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore
Training Course on Threat Hunting with Malware Analysis Techniques is designed to equip cybersecurity professionals with hands-on skills in proactive threat detection and malware reverse engineering.
5 days
Accra, Addis Ababa, Bangkok, Cape Town, Dubai, Istanbul, Kigali, Nairobi, Singapore