Digital Forensics Courses
Comprehensive Digital Forensics training programs for professionals
Comprehensive Digital Forensics training programs for professionals
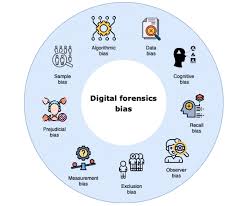
Training Course on Ethics and Bias in Artificial Intelligence/Machine Learning for Digital Forensics provides digital forensic professionals with the critical knowledge and practical skills to navigate the complex interplay between cutting-edge AI/ML applications and the imperative of maintaining fairness, transparency, and accountability in forensic outcomes.
Training Course on Ethics and Bias in Artificial Intelligence/Machine Learning for Digital Forensics provides digital forensic professionals with the critical knowledge and practical skills to navigate the complex interplay between cutting-edge AI/ML applications and the imperative of maintaining fairness, transparency, and accountability in forensic outcomes.
Training Course on Malware Campaign Tracking and Attribution equips participants with tactical knowledge and practical techniques for malware reverse engineering, infrastructure pivoting, behavioral analytics, threat actor profiling, and intelligence enrichment for attribution.
Training Course on Malware Campaign Tracking and Attribution equips participants with tactical knowledge and practical techniques for malware reverse engineering, infrastructure pivoting, behavioral analytics, threat actor profiling, and intelligence enrichment for attribution.

Training Course on Network Signatures for Malware Detection is designed to equip cybersecurity professionals with in-depth knowledge and actionable skills in identifying, analyzing, and defending against advanced persistent threats (APTs) using signature-based detection techniques.
Training Course on Network Signatures for Malware Detection is designed to equip cybersecurity professionals with in-depth knowledge and actionable skills in identifying, analyzing, and defending against advanced persistent threats (APTs) using signature-based detection techniques.

Training Course on Automating Malware Analysis Workflows is tailored for cybersecurity professionals, malware analysts, and SOC engineers seeking to revolutionize their incident response, reverse engineering, and malware triage processes through automation, scripting, and cloud-based integrations.
Training Course on Automating Malware Analysis Workflows is tailored for cybersecurity professionals, malware analysts, and SOC engineers seeking to revolutionize their incident response, reverse engineering, and malware triage processes through automation, scripting, and cloud-based integrations.
Training Course on Detecting Fileless Malware and Living-Off-The-Land Binaries is designed for cybersecurity professionals, SOC analysts, incident responders, and threat hunters who are looking to enhance their advanced threat detection skill set.
Training Course on Detecting Fileless Malware and Living-Off-The-Land Binaries is designed for cybersecurity professionals, SOC analysts, incident responders, and threat hunters who are looking to enhance their advanced threat detection skill set.

Training Course on Scripting for Malware Analysis is designed to equip learners with cutting-edge scripting techniques to identify, dissect, and neutralize modern malware threats.
Training Course on Scripting for Malware Analysis is designed to equip learners with cutting-edge scripting techniques to identify, dissect, and neutralize modern malware threats.

Training Course on Threat Hunting with Malware Analysis Techniques is designed to equip cybersecurity professionals with hands-on skills in proactive threat detection and malware reverse engineering.
Training Course on Threat Hunting with Malware Analysis Techniques is designed to equip cybersecurity professionals with hands-on skills in proactive threat detection and malware reverse engineering.

Training Course on Analyzing IoT Malware and Botnets is designed to equip cybersecurity professionals, analysts, and researchers with in-depth skills to detect, analyze, and mitigate IoT malware threats using real-world scenarios, automated tools, and forensic methodologies.
Training Course on Analyzing IoT Malware and Botnets is designed to equip cybersecurity professionals, analysts, and researchers with in-depth skills to detect, analyze, and mitigate IoT malware threats using real-world scenarios, automated tools, and forensic methodologies.

Training Course on Cloud-Based Malware Analysis Environments equips learners with the knowledge to deploy, manage, and utilize scalable cloud-based sandboxing systems, behavioral malware analysis tools, and automation frameworks.
Training Course on Cloud-Based Malware Analysis Environments equips learners with the knowledge to deploy, manage, and utilize scalable cloud-based sandboxing systems, behavioral malware analysis tools, and automation frameworks.

Training Course on AI ML for Malware Detection and Classification is designed to equip cybersecurity professionals, data scientists, and IT leaders with the advanced skills necessary to implement AI/ML-based malware detection techniques.
Training Course on AI ML for Malware Detection and Classification is designed to equip cybersecurity professionals, data scientists, and IT leaders with the advanced skills necessary to implement AI/ML-based malware detection techniques.

Training Course on Firmware and Embedded Malware Analysis is designed to empower cybersecurity professionals, reverse engineers, and security analysts with the skills required to dissect, analyze, and defend against malicious firmware threats targeting embedded systems and IoT devices.
Training Course on Firmware and Embedded Malware Analysis is designed to empower cybersecurity professionals, reverse engineers, and security analysts with the skills required to dissect, analyze, and defend against malicious firmware threats targeting embedded systems and IoT devices.

Training Course on Ransomware Negotiation and Decryption Tools equips cybersecurity professionals, IT administrators, and risk managers with the tactical and strategic capabilities to handle ransomware incidents efficiently and legally.
Training Course on Ransomware Negotiation and Decryption Tools equips cybersecurity professionals, IT administrators, and risk managers with the tactical and strategic capabilities to handle ransomware incidents efficiently and legally.